Key logger is something that records the keystrokes. In simple words, it records everything you type and keeps saving the data recorded it in a text file. A key logger is meant to be used for positive purposes like spying on your own computer or on your children's computer. But these are mostly used for malicious purposes by attackers to steal sensitive data of victims. This sensitive data might be anything like his email ID,password,banking details etc.
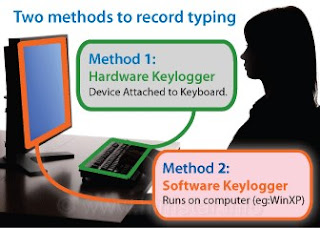
A key logger might be a software or hardware.
Software Keylogger : A software key logger can be of further two types.
Local Keylogger : A local key logger is a software that is installed on a computer, records the keystrokes typed and save them into a text file on local machine. An attacker needs to have a physical access to victim's computer to steal data through local key loggers.
Remote Keylogger : A remote key logger is exactly same as local key logger. But one additional thing, it does that is it keep sending the text files in which data has been recorded to a remote location as specified the user. The remote location can be your email ID,ftp account etc.So Attacker doesn't need to have physical access on victim's computer.
Hardware Keylogger : A hardware key logger is something like normal USB drive that is plugged between keyboard plug and USB socket. It has an inbuilt memory that records all the keystrokes.
The obvious limitation of hardware key loggers is that there physical presence can be easily detected.
Method of Attacker in Using Remote Keylogger :
1. Attacker creates a malicious executable .exe file of size in kbs.
2. Attacker might hide this .exe file behind any genuine file like a song or image. Attacker gives this file to victim and victim is supposed to double click on it.
3. As the victim clicks it, the keylogger gets installed in victim's PC without his knowledge. It secretly
keeps saving the text typed or keystrokes hit by the victim (and may be a lots of other information of victim activities). As the victim connects to Internet, those files are sent to remote location as configured by attacker.
Note : It was just a basic theoretical guide of keyloggers. A key logger has many more additional features.




 About UsFind out working team
About UsFind out working team AdverisementBoost your business at
AdverisementBoost your business at Need Help?Just send us a
Need Help?Just send us a We are SocialTake us near to you,
We are SocialTake us near to you,
3 comments: On keylogger The Basics
Article material which is strongly related your readers.
It's beneficial to permit attendees to create posts on your blog.
They would like to find out about strengths instead.
Of course, with today's technology, such as the Kindle, market reading without
ever touching report.
Oblivion was and is still a game title of merit, something which is really an element of
artwork.
good one 🙂